Thank you!
The form has been successfully submitted
The form has been successfully submitted
Oops! Something went wrong, please try again

SIP Trunk has become the standard for modern voice infrastructure. It is scalable, cost-efficient, and flexible. But together with these advantages come risks: malicious traffic, fraud, data interception, overloads, and attempts to take control of the voice gateway.
Protecting SIP Trunk is a critically important part of business security, because any failure in voice channels immediately affects sales, support, and reputation.
The stability of SIP Trunk is the result of properly built protection. DID Global not only identifies threats but actively neutralizes them through multi-layered security mechanisms. Let’s look at the main risks and how our infrastructure blocks them in practice.
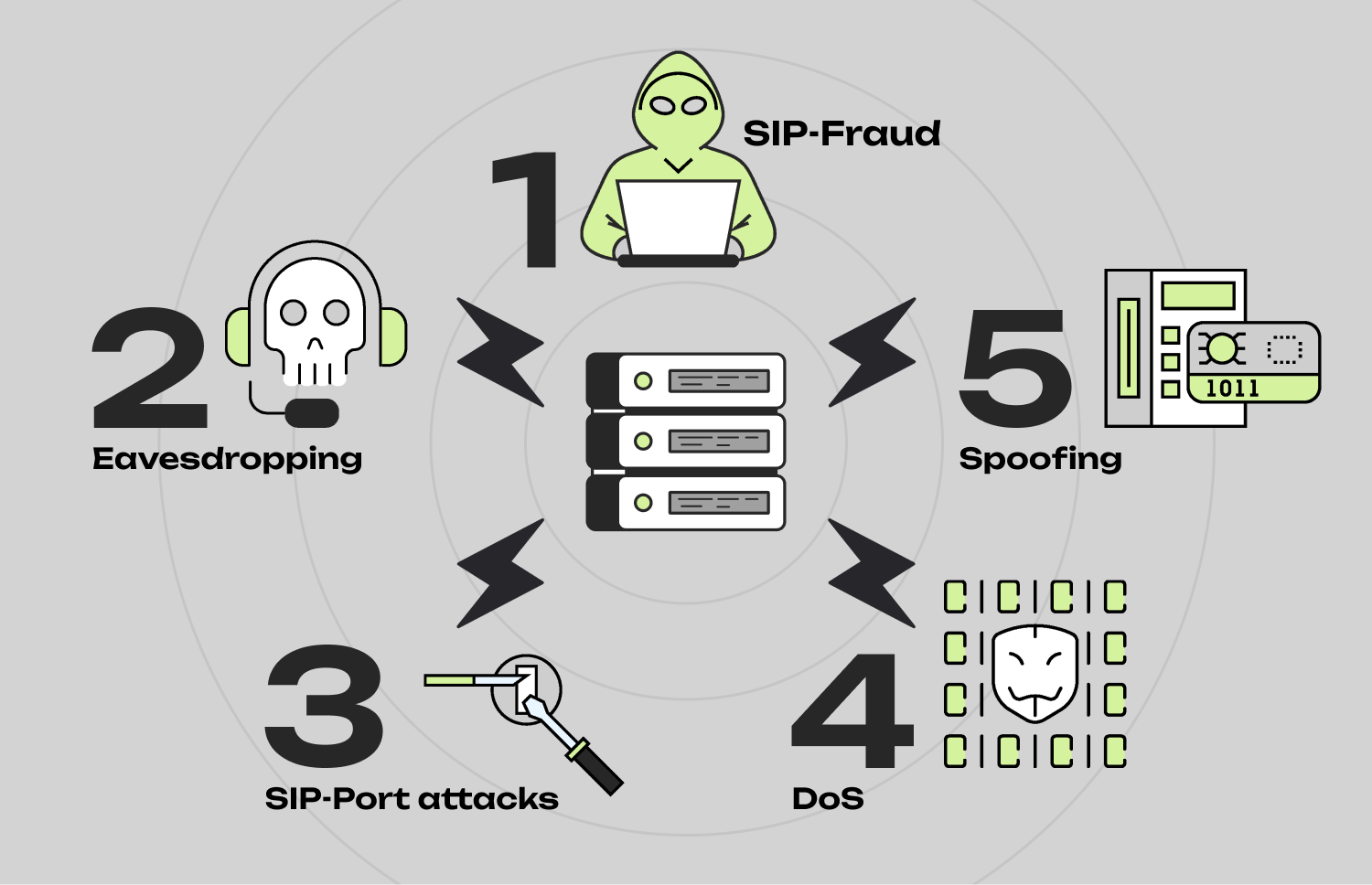
SIP traffic moves through IP networks, which makes it vulnerable to attacks that did not exist in traditional telephony. The most common threats include:
Attacks may look like a spike in outgoing calls at unusual hours or attempts to establish connections to premium-rate numbers.
Companies face not only technical failures but direct financial losses.
DID Global case:
One e-commerce client received hundreds of suspicious calls in a single night. After moving their SIP traffic to DID Global routes and activating anti-fraud algorithms, the suspicious calls were blocked within 37 seconds, preventing potential losses of more than €4,000.
Unencrypted traffic can be intercepted and listened to. For industries with strict regulations (healthcare, fintech, insurance), this is a critical risk.
Bots send thousands of requests trying to brute-force passwords for PBX systems, IP phones, or gateways.
The worst-case scenario is full control over the phone system.
Such attacks aim to “take down” the SIP server, making the contact center unavailable.
This is especially dangerous during peak seasons, where every missed call = a lost customer.
Manipulation of the sender’s number can lead to phishing schemes or to your number being blocked by carriers due to damaged reputation.

SIP Trunk protection consists of several layers – network-level, protocol-level, and operational.
This prevents eavesdropping, interception, or modification of data.
For industries with confidentiality requirements, this is a must-have.
DID Global experience:
After switching to TLS+SRTP, one EU medical service successfully passed a compliance audit by the local regulator. The recorded level of traffic interception decreased to 0%.
Standard network firewalls do not recognize the SIP protocol deeply enough.
Specialized SIP firewalls:
DID Global uses behavioral monitoring – algorithms track unusual call patterns, sudden spikes, or geographic anomalies.
This drastically reduces the attack surface.
For stable operation, it is important to monitor:
DID Global companies gain access to analytics with real-time reaction.
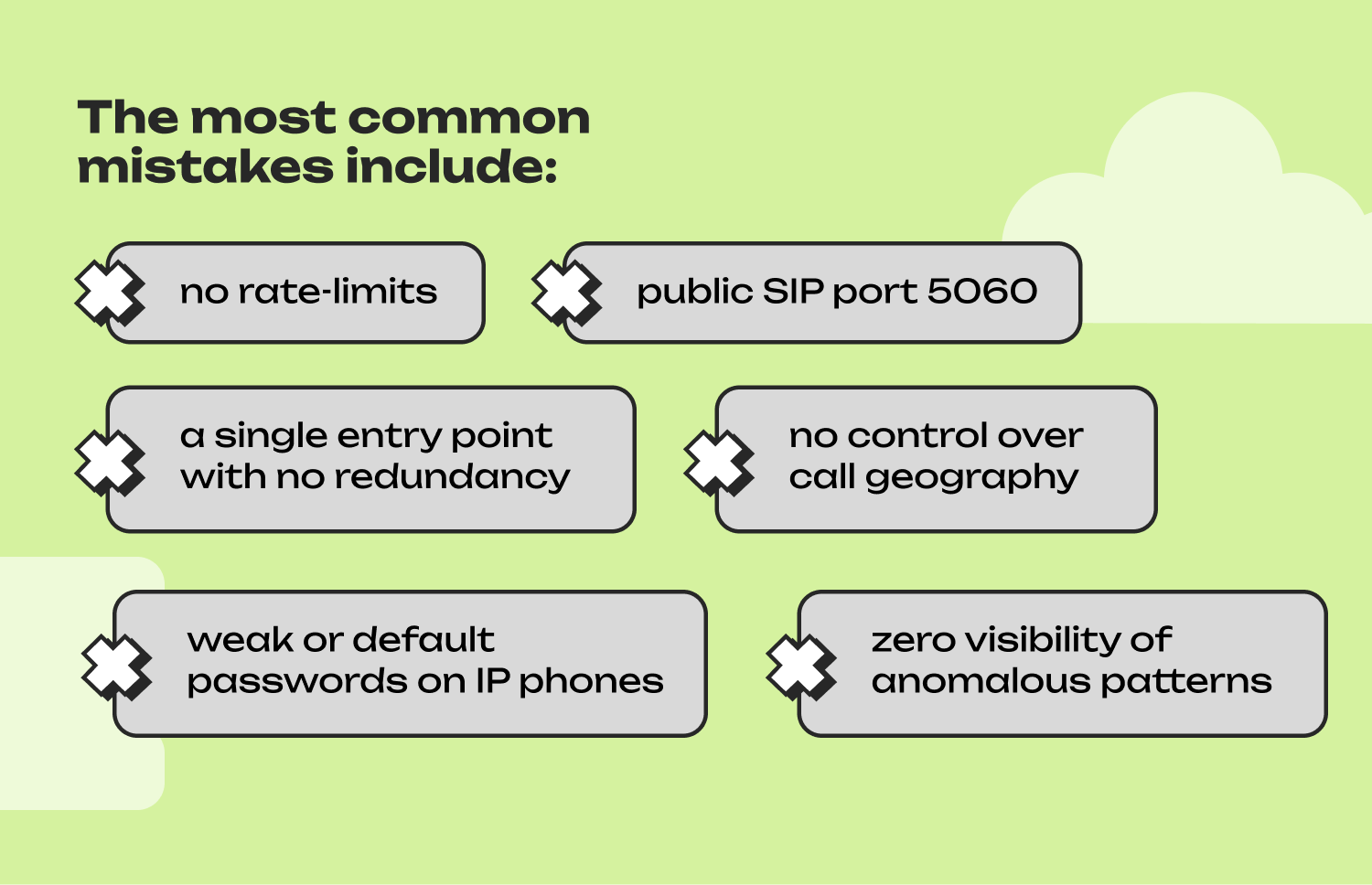
Despite modern security tools, most SIP traffic incidents occur not due to sophisticated attacks but because of basic configuration gaps. Many companies run the system “somehow” until one day anomalous traffic appears, suspicious registrations occur, or costs suddenly spike.
The most common mistakes include:
SIP infrastructure reliability is easy to overestimate: most companies believe it is secure until the first fraud attempt or routing failure appears. To assess the real condition, you only need to go through several critical points:
If even one point raises doubts, it is a signal that the infrastructure operates without sufficient protection and may become vulnerable to fraud, disruptions, or carrier blocks.
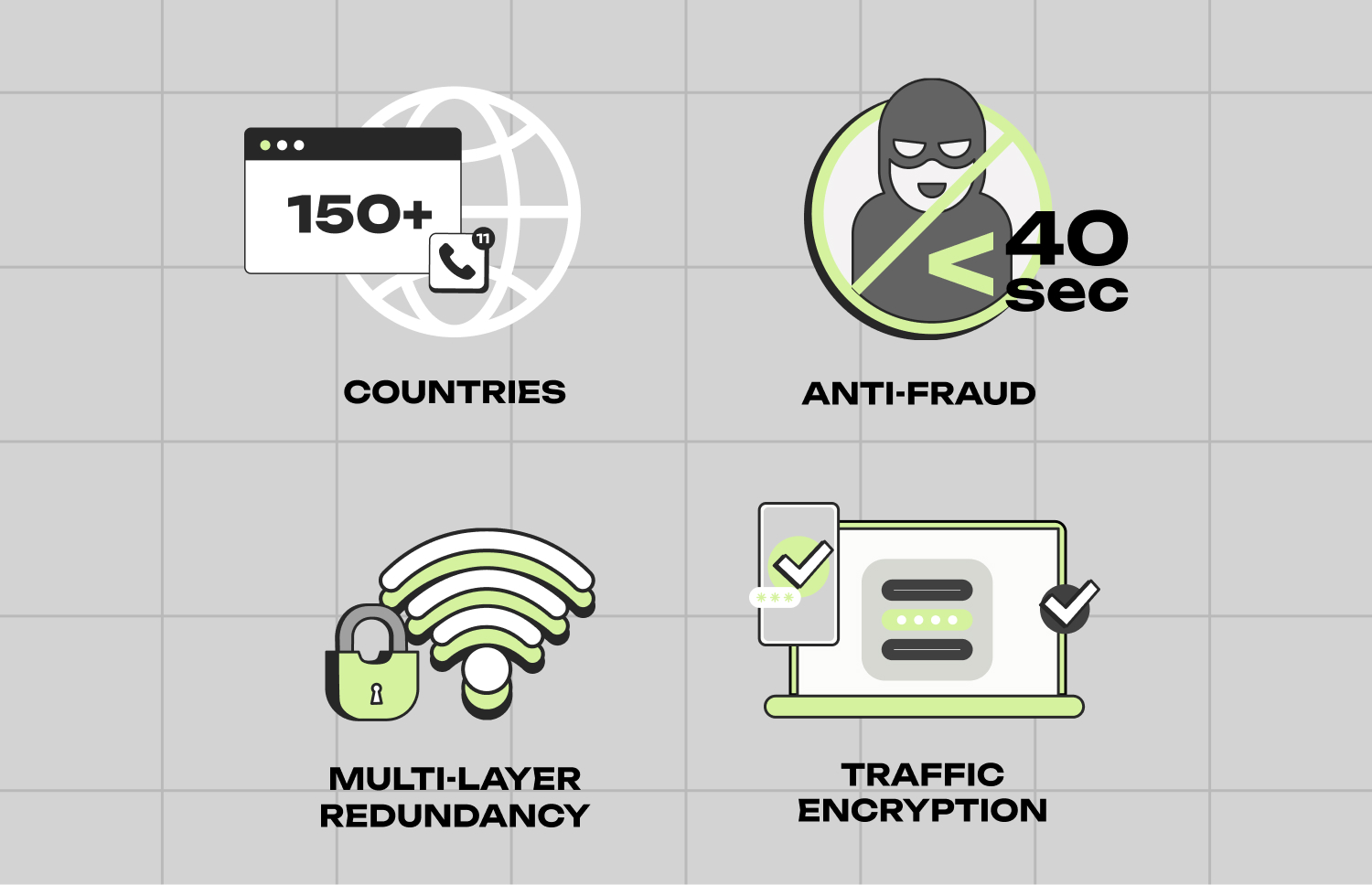
Companies working with large call volumes or distributed teams are especially sensitive to the quality and security of routing. DID Global’s infrastructure is designed to minimize risks and ensure stability even in complex international scenarios.
Main advantages include:
DID Global case:
A European retail network faced a DoS attack on its SIP port, making the contact center unavailable. After switching to DID Global, attacks were filtered at the carrier router level, without involving the client’s internal resources. Service availability increased from 97.8% to 99.995%.
SIP Trunk is flexible, scalable, and cost-efficient, but only with proper security.
Encryption, anti-fraud, firewalls, monitoring, and the right provider determine whether a business can operate reliably under growing threats.
DID Global’s infrastructure helps companies across Europe and worldwide build secure voice systems that withstand heavy load, scale without risk, and operate predictably.